what are inside/internal attacks?
These attacks usually come from people within the organization’s security perimeter. Generally, insiders can be categorized into pure insiders, associate insiders, and affiliated insiders. Pure insiders usually have authorized physical access like smart card keys, and have network login server credentials. An elevated pure insider likes system administrator in the ICT department and dissatisfied employees.
These types of pure insider attackers are very dangerous and effective .it cannot be controlled by the organization very easily. Associate insiders are people that have limited but authorized physical access and don’t have a direct login credential. they are usually part-time people, spies and maintenance people. Insider affiliates are not employees but they have a direct connection with the employee. they could be a boyfriend, girlfriend, wife and soon.
what are Outside/External attacks?
Attacks that come from outside of the organization by unauthorized people. most of the organizations are investing more money to defend outsider attacks. The commonly affected area is the servers of the organization that is connected to the global network. This is the most vulnerable area when it comes to outsider attacks.
Possible inside and outside attacks.
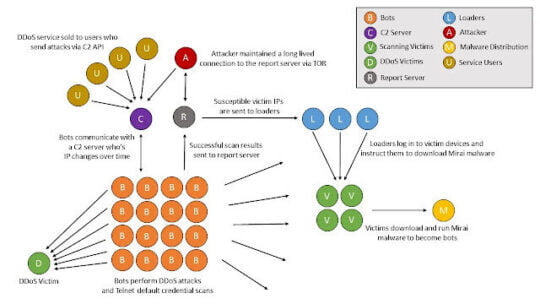
Distributed denial of service attack: – This is one of the effective active type attacks that affect the operations of the servers. the attacker does have control over a group of zombies and create legitimate TCP sessions to the web server from those zombies. So, tap connection from the legitimate user will be dropped.so this will negatively affect organization operation. For example, users cannot be able to do online orders or access organization resources. (Rapid7. 2017).
Phishing attack: – This is a social engineering skill attack. the effectiveness of these phishing attacks is fully depending on the awareness of the people. A phishing attack is done by an attacker who pretending as legitimate so people will believe it and do the action. Email phishing is a common way of attacking the victim.
Anthem was also affected by this type of attack; the attacker did send a phishing email to a group of anthem employees with the malware attachment. The employee might think that email comes from the anthem. So that he or she might be clicked on the attachment, due that malware could be able to execute on the computer without his/her knowledge. And hacker could be able to find the credentials via the help of that malware. (Rapid7. 2017).
Malware attacks: – malware is malicious software such as viruses, worms, and trojans, ransomware. that cause damage to the computer systems. Most of the malware is executed by user action and some others automatically infected from another host or storage device. If ransomware infected on the computer of the financial division then they can’t do anything related to the day to day financial activities. So, it will heavily affect business continuity. (Rapid7. 2017).
SQL injection: – this is a type of attack that allows an attacker to dump the database details using malicious SQL queries. poorly designed web apps are vulnerable to this attack. Web apps and the databases are running on company servers. They have tons of sensitive data. The attacker can. bypass the authentication mechanism modify, delete and add the data. so, company secret will expose. (Rapid7. 2017).
Tools used to defend against insider and outsider attacks
Antimalware software: – this is a complete solution for all kinds of malware rather than tradition antivirus software. but all the virus definitions must be up to date. Hence it can detect the malware easily otherwise it can’t do anything. Malware detection can be categorized into signature-based detection and anomaly-based detection.
Signature-based detection check binary code of the file with well-known malware. The drawback of this detection is it can’t detect any newly created fresh malicious software, on the other hand, anomaly-based detection is detecting by monitoring the behavior of the file. (Solutions, P, 2017).
PhishCatch:– This is a phishing detection tool that is developed by IEEE. it uses a heuristic-based algorithm that has an 80% catch rate and 99% accuracy. If it finds the phishing attack then alert the user about the attack instantly. Still, it doesn’t have a 100% detection rate so be aware anytime is a much more efficient way. Ieeexplore.ieee.org. (2017).
IDS/IPS– Most organizations do spend a huge amount of money on defending outsider attacks. They have firewalls to prevent incoming traffics but nothing for outgoing traffics. Firewalls are not the intelligent device they will work with the set of definitions of rules. so that proper intrusion systems should be implemented for inbound and outbound traffics. Some limited amounts of throughput should be allowed for outbound traffic. if that throughput exceeded the limit then an alert should be displayed to the IT people.
CDN with DDOS mitigation cloud: – denial of services which is less effective and it can be easily blocked by access control list or firewall because it is the single host. But DDOS very effective it needs special attention. For web servers, CDN can be used. It will handle the HTTP or any other request and block the suspicious traffic request. Cloudflare is one of the best service providers. But if the attacker finds the actual IP address of the server then it is a disaster. (Rachel Kartch, 2016)
Database IDS: – this type of ids monitors the network traffic and detect suspicious activities against the database. (SearchSecurity, 2017).
Microsoft source code analyzer can be used for finding vulnerabilities in .net apps and ensure that the web app is designed properly. (Blogs.msdn.microsoft.com, 2017).