IP camera uses internet protocol to transfer the Realtime video feed. it generates the images from digital data directly. Commonly, IP camera uses POE technology to get the power while the Wireless IP camera has an inbuilt battery or get power from electric cord or solar panel. Unlike the analog camera, IP camera encodes and processes the video itself and streams the video feed to NVR for storing or remote viewing purpose.
NVR does the additional video compression processing and meta-tagging. The IP camera has improved features such as better object detection, progressive scanning, high resolution, IR illuminator, better night vision, high frame rate, remote monitoring, wide dynamic range, intrusion alarm, better motion detection.
Security Goals
Feeling of Safety
Deployment of security cameras makes employers feeling of a safe environment. Thus, reduces the fear of crime. Feeling as the victim of crime reduces the productivity of the work as well as resist the concentration on business goals. According to the security standard, the feeling of safety environment is a must and fundamental need.
Assets Protection
In terms of business, Assets are the properties of the company which has values. Assets can be categorized in to tangible and non-tangible. IP cameras focus on tangible assets protection. non-tangle protection is depending on tangible asset protection. For example, if a tangible asset like a laptop lost, a non-tangible asset like data also lost. Loss of very import asset of the company causes serious damage to business continuity, imagine a hard drive contains a trade secret and it has been stolen by their competitors.
Ensure Compliance
IP camera Surveillance ensures that the employees are following the standards. It helps to prevent the improper handling of equipment and other criminal activities. To protect the company and its value, employees should adhere to the security standards and guidelines.
Evidence and investigation.
Surveillance cameras play a huge role when it comes to finding evidence and conducting an investigation of any past on-premises crime events. recorded video is the best evidence to a successful investigation. It helps to punish the criminals.
Deterrence
It is one of the features that demotivate people from engaging in criminal activities. Because people think that they are being watched and security officials can easily identify and arrest them. This will not prevent all the criminals but prevent few criminal activities.
Potential Adversaries and Threats
Being Hacked
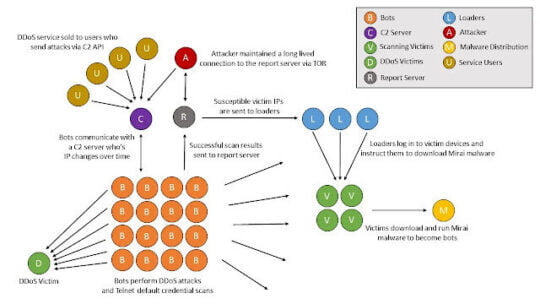
IP cameras are based on internet protocol, therefore accessing camera video feeds remotely become popular, owners can access the video in any internet-enabled smart gadgets like smartphone or tablet. Commonly, the cloud is used for storage. Therefore, IP cameras are exposing themselves to the internet. Thus, creates an opportunity for hackers. It has been concluded that IoT devices including IP cameras were used by Mirai malware to conduct DDOS attacks on web servers.
Vandalism
It refers to any offense that done by the criminals which include breaking the camera, cutting the power cables of the camera, spraying paint or sticking sticker to obstructing the camera view.
Spiders and Bugs
Spiders and bugs are attracted to the infrared light emitted from the camera. It obstructs the view and triggers alarm if the motion sensor is enabled.
Potential Weaknesses
Insecure Authentication
IP camera uses the user name and password authentication mechanism to access the video feeds from camera and take control of it . in this context, the security of the IP camera is depending on the strength of the password and the usage of multi-factor authentication. If the password remains unchanged and the default password is used, it is vulnerable to brute force attack. Techcrunch reported that massive botnet attack has been conducted against amazon, twitter and other sites using IOT devices including IP camera which uses the default password. therefore, Mirai malware exploited easily.
Firmware Bugs
Firmware is a software which is permanently programmed on device-specific hardware. It controls the low-level functionalities of the device. Software is not 100% perfect like any other products. New bugs are identified over time. These bugs introduce new vulnerabilities. These vulnerabilities often help to exploit the camera system and access the video feeds. ICS issued an adversary for Hikvision IP Cameras about the vulnerabilities in firmware such as improper authentication occurs when an application does not correctly authenticate the users, the firmware software stores the password in the configuration file.
The Limited Angle of View
Commonly deployed IP cameras have the angle of view limitation. They can monitor a limited area. These cameras do not monitor any abnormal activities that happen outside of their angle of view. Criminals can do any harmful activities to the cameras from the backside, and therefore the person remains unidentified.
Potential Defenses
- Never use the default credential for authentication. set the password to a minimum 8 characters long, it should include at least one upper case letter, lower case letter, and symbol.
- If camera feed wants to access via the internet, make sure to use a virtual private network. Implement multi-factor authentication. always use https variant to communicate with media server and strong encryption algorithm should be used.
- Check for firmware update regularly and enable automatic firmware update if the IP camera does support it.
- If it is a WIFI IP camera, make sure to enable WPA 2 rather than WEP security protocol.
- Deploy multiple cameras in important areas. Fish-eye cameras can be used to solve view angle limitation issues.
Conclusion
Every technology has strengths, weaknesses, and threats. Therefore, the users should follow the security standards and guidelines to minimize effect caused using the above technology. Because as discussed above, the user’s mistake greatly affects the reputation of the technology. If the security standards and guidelines are followed, this technology helps to achieve the above-mentioned security goals in the long term.