HTTP is an application layer protocol used to access web content from and push web content to a web server which is stateless in nature. HTTP flood attack is a type of Distributed denial of service that designed to overload the web server with HTTP requests from zombie hosts and interrupts service from access legitimate user requests.
Due to the nature of the HTTP protocol, it is very difficult to distinguish the zombie’s requests and user’s requests from the web server’s point of view. Generally, each zombie sends small numbers of packets and thus look like a legitimate user. HTTP flood attacks can be categorized as HTTP-get method attacks and HTTP-post method attacks. The HTTP Get method is used to fetch the webpage contents from a web server and the HTTP-post method is used to push the content to the web server.
Further, HTTP flood DDoS attacks can be categorized into two based on their topology structure. they are centralized and distributed botnets. A centralized botnet is the most commonly used topology structure. (E. Alomari, S. Manickam, B. B. Gupta, P. Singh, and M. Anbar, 2014)
1. Methodology
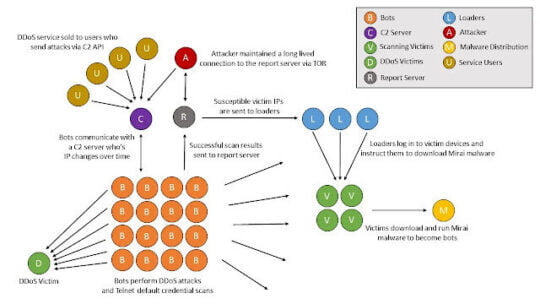
Centralized Structure of an HTTP-based DDOS Attack
HTTP flood attack process involves the attacker keeping a command and control server, mostly he/she may have physical access or a cloud-based server. The C&C server maintains communications with bots also known as zombies and the C&C server changes its IP address over a specific time to stay secure. The attacker instructs bots to send HTTP-get or HTTP-post requests to the target DDoS victim through the C&C server.
Another challenging part is spreading bot malware to vulnerable hosts on the internet. This can be done in various ways such as downloading nulled software, clicking untrusted links in the email, finding the hosts that have a default password for Telnet or SSH, etc. once the bot malware is installed on a normal user’s PC or host, it will become a part of a private bot network. Normal users cannot be able to identify easily because it will not generate high noise. Black energy, Zemra, and Mirai are some examples of bot malware. (E. Alomari, S. Manickam, B. B. Gupta, P. Singh, and M. Anbar, 2014)
2. Real word hits
- According to (BBC News, 2017) Ukraine’s national postal service’s website and online parcel tracking system has been hit by DDOS attack hackers and it long lasted for more than 13 hours. The website and online parcel tracking system went offline.
- According to (Whittaker, 2016) BBC’s website’s root domain including on-demand and radio, the player suffered from an outage for 3 hours. Firstly, it was considered a technical issue but later identified as a distributed denial of service attack.
3. Impacts
- Revenue loss may happen.
- Productivity loss, product work may be halted due to server system shutdown.
- If the service is not available when needed, then the organization’s reputation may be damaged.
- It may damage the server hardware.
- It may cause customer loss.
4. Best practices.
- Host the website in multiple data centers across different countries.
- Implement a content delivery network for the website, so the HTTP request will be directed to CDN servers first.
- Tune the server to keep alive off
- Apply Apache custom modules such as mod_antiloris and mod_limitipconn
- Implement and configure web application firewall properly.
- Implement network monitoring solutions (Indusface, 2017)
- Create a null route in the router and redirect the traffic if any anomaly is detected.
- Block known suspicious IP address range
- Implement next-generation firewall and configure botnet filtering.
- Implement IPS